Home > Security Settings
Categories: Security
(Last Updated On: September 21, 2021)
About This Article
The purpose of this article is to provide a comprehensive overview of the Security Settings tab.
Security Settings
Only your account owner can change your security settings.
*The new security settings are available on enterprise accounts.
Password Rules
Password complexity
Change the password requirements to increase the difficulty of password cracking
Every time you increase the requirements of your passwords all your users passwords will be expired. For your users sake, keep this to a minimum.
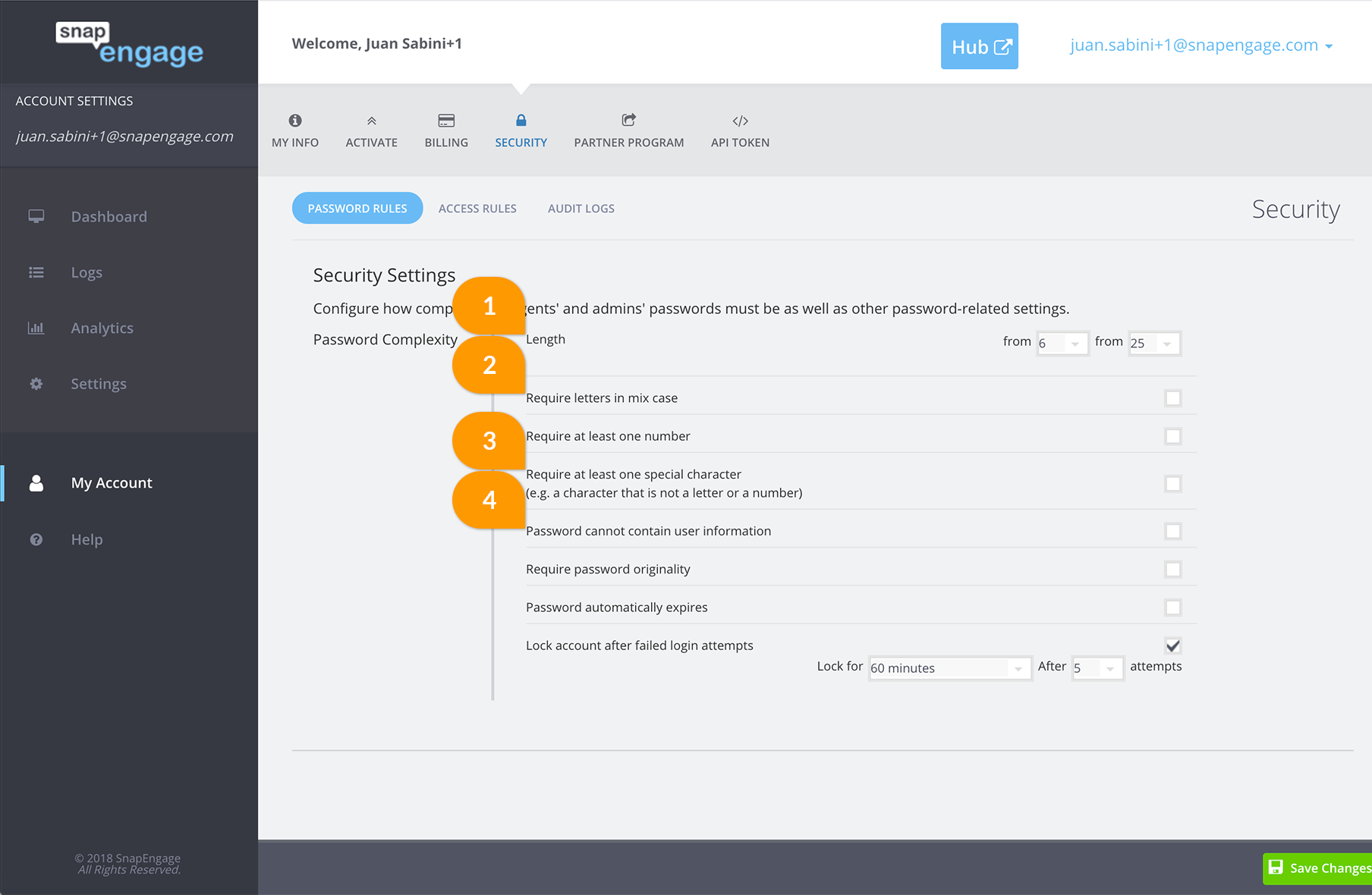
1. Length
Require your users to have a certain number of characters in your password. This is important because the time it would theoretically take to crack a password increases exponentially with each added character.
2. Require letters in mix case
Require your users to combine both upper case and lower case character. I.e ‘notsafepassword’ wouldn’t be accepted ‘safePassword’ would.
3. Require at least one number + Require at least one special character.
Enabling “Require at least one number” will require your users to have at least one number in their password. For example ‘notsafepassword’ wouldn’t be accepted but ‘safepassword1’ would or ‘saf3password’ would also be accepted.
Enabling “Require at least one special character” will require your users to have at least one special character (non-alphabetic and non-numeric). For example ‘notsafepassword’ wouldn’t be accepted but ‘safepassword!’ would or ‘safe+password’ would also be accepted.
4. Password cannot contain user information
Make sure that your users aren’t using parts of their login information in their password. This is important because when trying to guess someones password it’s common practice to try to get information from your users login. For example, [email protected] wouldn’t be allowed to user name or surname in his/hers password.
Password handling
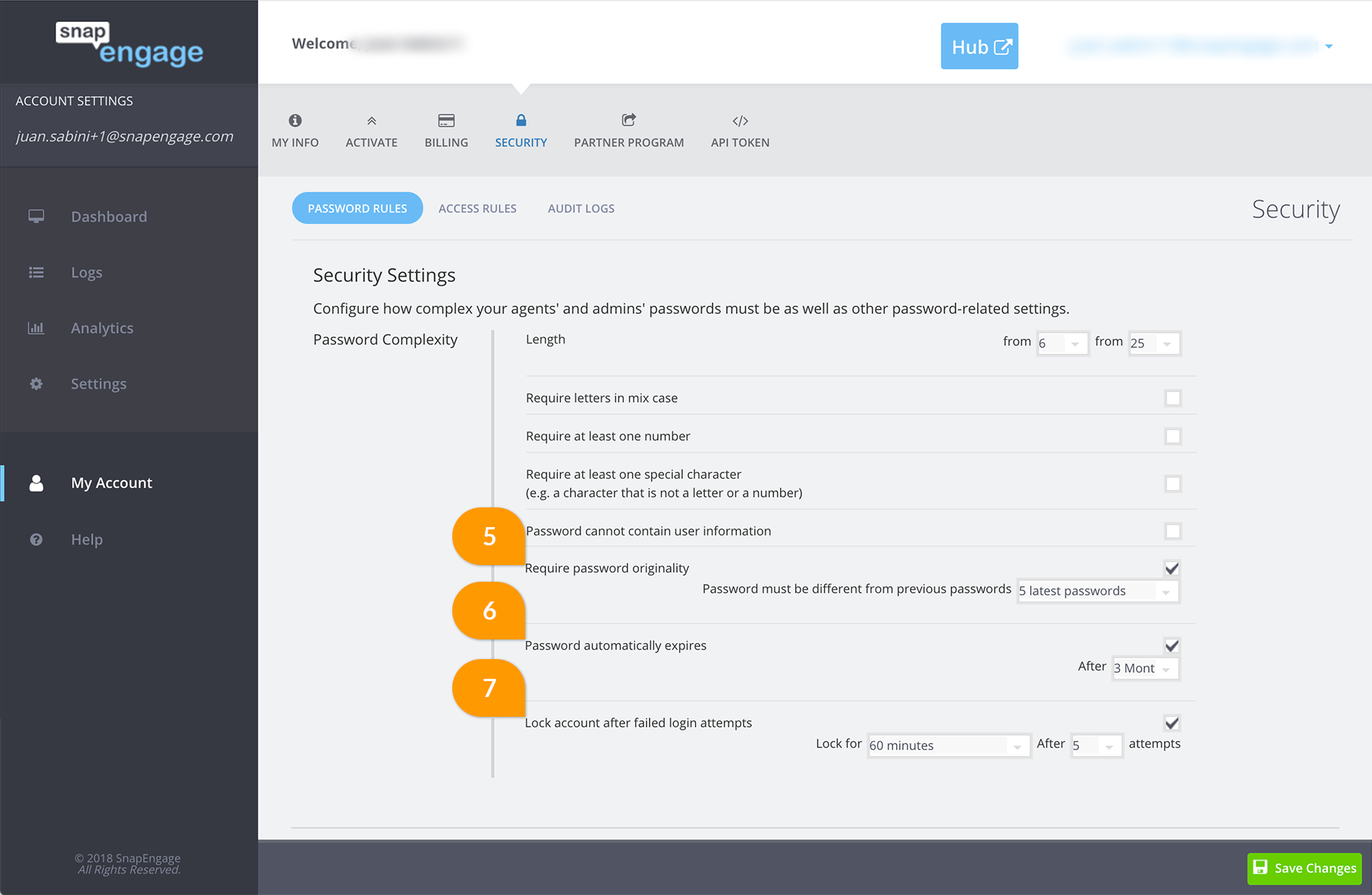
5. Require password originality
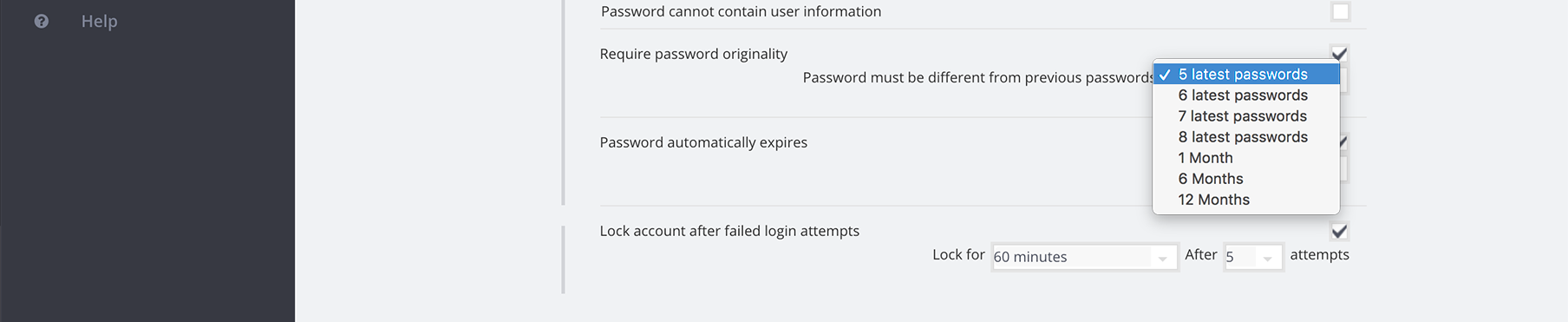
When a user renews his or hers password this option forbids re-usage of old passwords. You can make sure that the password hasn’t been used before for the last 5 to 8 passwords or for any password that has been used for the last 1, 6 or 12 months.
If two password settings get compared, we would consider the ‘x last passwords’ option more secure than ‘passwords in the last x months’.
Why would I want to prohibit password reuse?
Because of risk mitigation and human psychology. What would you do if you become aware of a password leak in your administration? The easiest would be to just ask your account owner to reset all the user passwords. However, we humans tend to be wary of changing our passwords. Many of us decide to just set our new password to our old password this would render the action useless. To make sure this does not happen you can disallow password reuse.
6. Password automatically expires
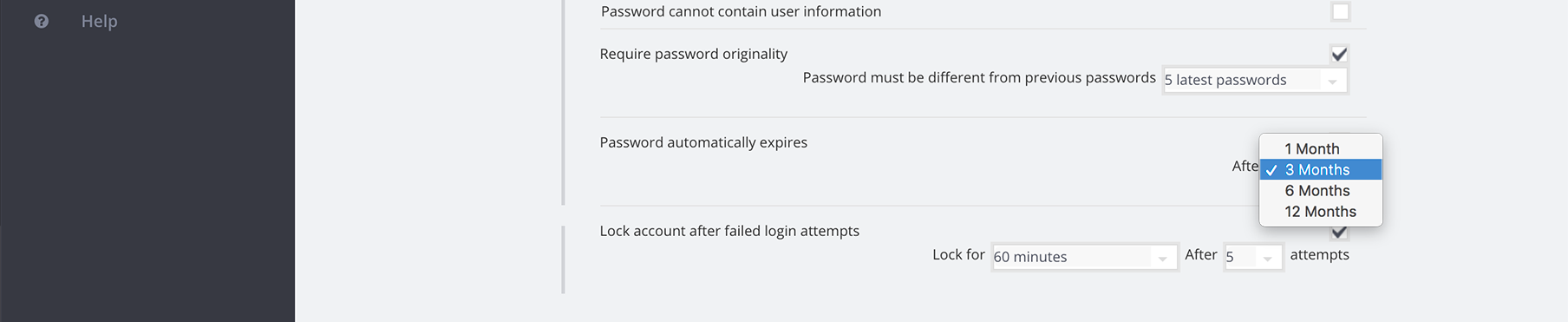
Require that your users renew their password on a recurring basis.
7. Lock account after failed login attempts
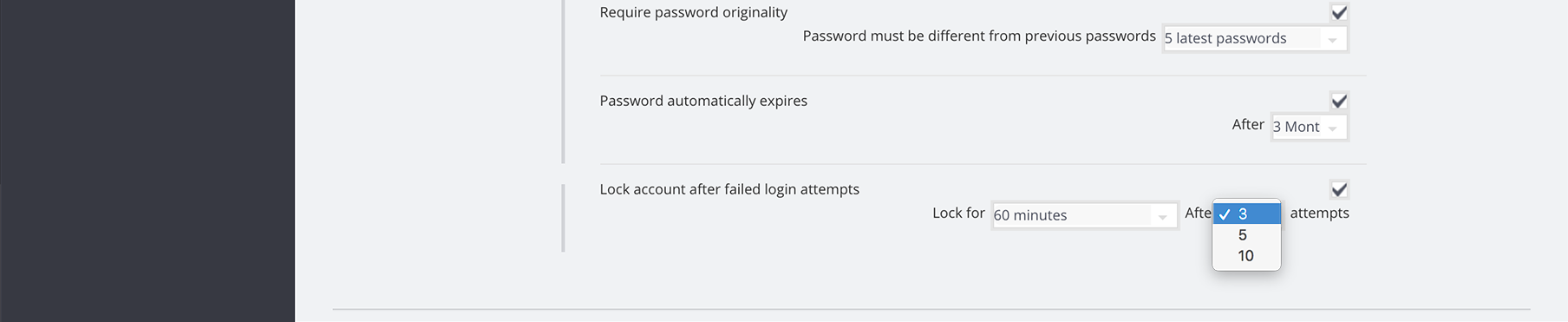
If the user has failed to login after a certain amount of attempts lock his/hers account. When a user’s account is locked the account will be unlocked again after a certain time (except if specifically required to lock permanently) or be unlocked from the admin dashboard.
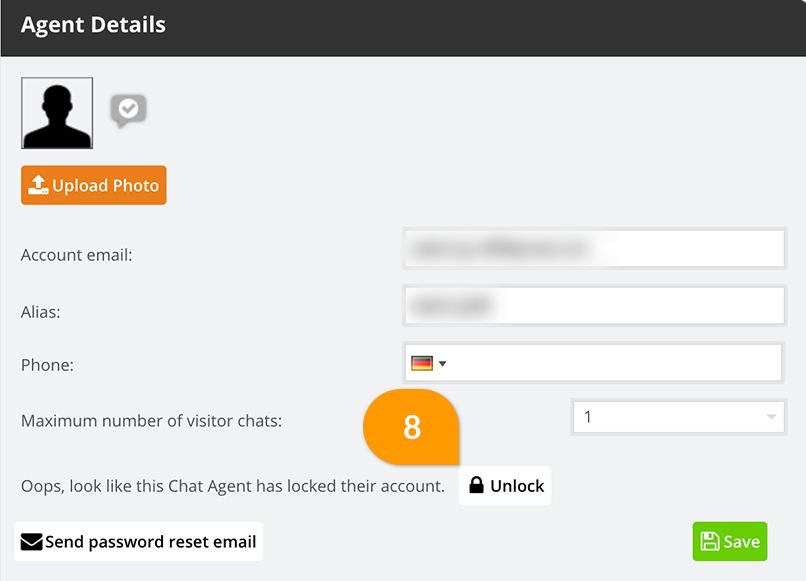
How to unlock a locked user account
If one of your user accounts has been locked, you can unlock this from the admin dashboard, by going to Settings -> Agent Settings -> click to “Edit” the individual agent’s profile, and clicking the button marked “8” below:
Access rules
Here you can configure who can access SnapEngage.
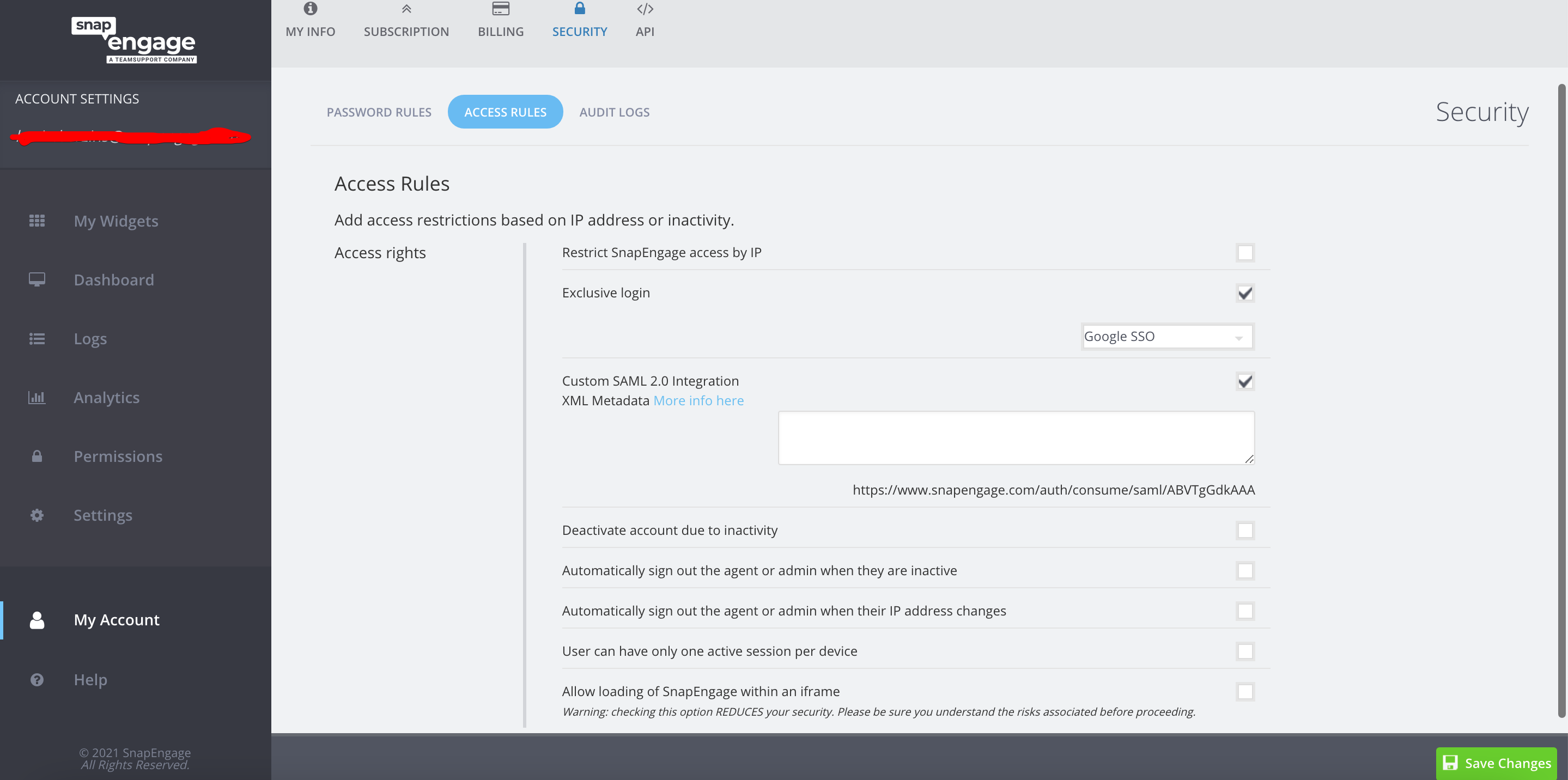
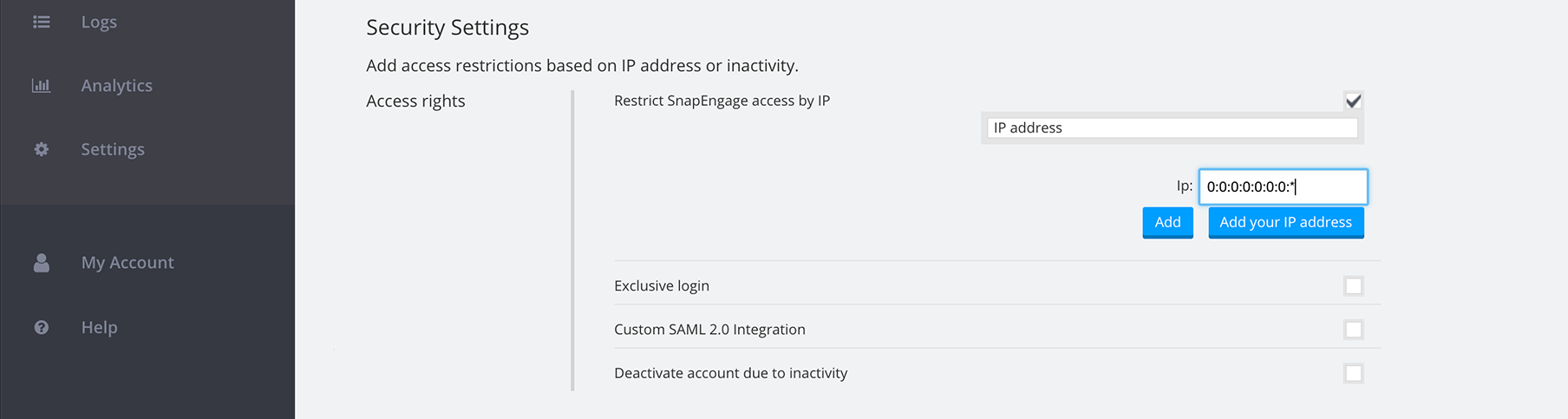
9. Restrict SnapEngage access by IP
You can restrict access to SnapEngage by IP addresses. You can either give specific IP addresses or you can use wildcards
Here are some examples of valid IP addresses.
- 192.168.1.1
- 192.168.1.*
- 192.168.1*.*
- 192.*.*.*
- 192.16*.1.1
- FE80:0000:0000:0000:0202:B3FF:FE1E:8329
- FE80:0000:0000:0000:*:B*:FE*:*
You can also get the IP address of your current computer. Here’s an example of us getting the IP (ipv6) from our current computer and we add a wildcard to that URL so that any IP that starts with “0:0:0:0:0:0:0:” will be accepted. This is useful if your organization shares a set amount of IP addresses. For example 192.168.1.1 – 192.168.1.255 then you would add 192.168.1.*
Please be aware that the IP restriction does not apply if you are using a custom SAML integration when logging in.
10. Exclusive Login
Checking this box means that anyone in your org will only be able to sign in via SSO. No one will be able to use their SnapEngage password to log in.
11. Custom SAML 2.0 Integration
You can connect SnapEngage with your Custom SAML 2.0 configuration so that users can sign in to SnapEngage using this, rather than their SnapEngage account details. You can read more about this here:
SSO via SAML 2.0 and Microsoft Active Directory Federation Server (ADFS) with SnapEngage
SSO via SAML and Okta with SnapEngage
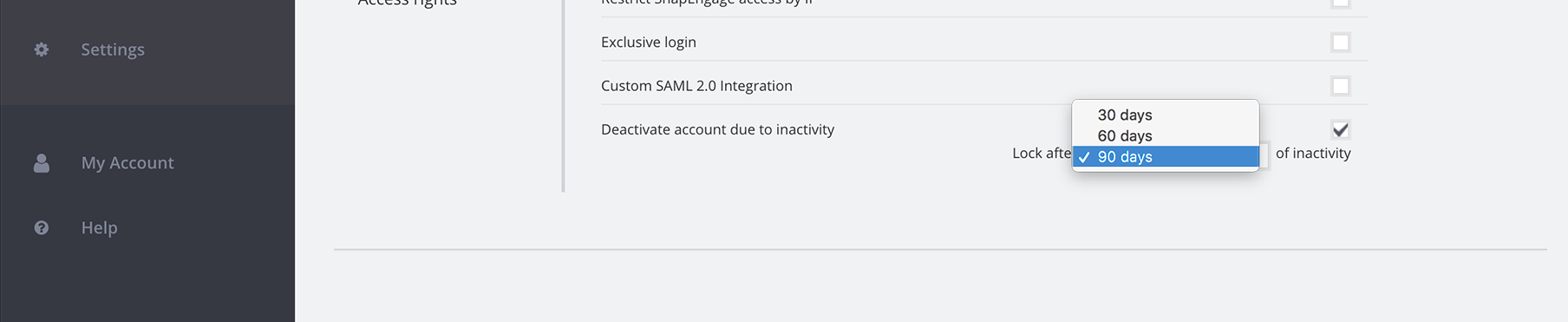
12. Deactivate account due to inactivity
Deactivate user accounts if a user hasn’t logged in for a set amount of time, you can find this option under My account > Security > Access rules.
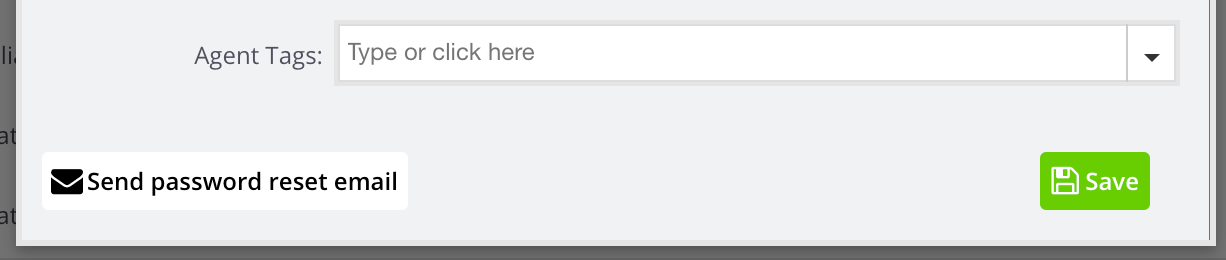
As an admin, if your agent receives an error that the account has been locked because of inactivity, you can send the agent a password reset link, by going to Settings -> Agent Settings -> click to “Edit” the affected agent’s profile -> Send password reset email:
Please be aware that the following security rules DO NOT apply to account owners :
- Manually locked account
- Locked due to inactivity
- IP restriction
13. Automatically sign out the agent or admin when they are inactive – This is used to sign out agents or admins if they become inactive after a given time.
14. Automatically sign out the agent or admin when their IP address changes – This will automatically sign out an agent or admin if they don’t match IP’s set in step 9.
15. User can have only one session per device – If an agent or admin is signed into multiple instances of SnapEngage admin dashboard or Hub this will only allow one per device.
16. Allow loading of SnapEngage within an iframe – . When this option is saved the permissions should propagate to all the agents within the org. This is used to allow SnapEngage to be inside and iframe for chrome more details here.
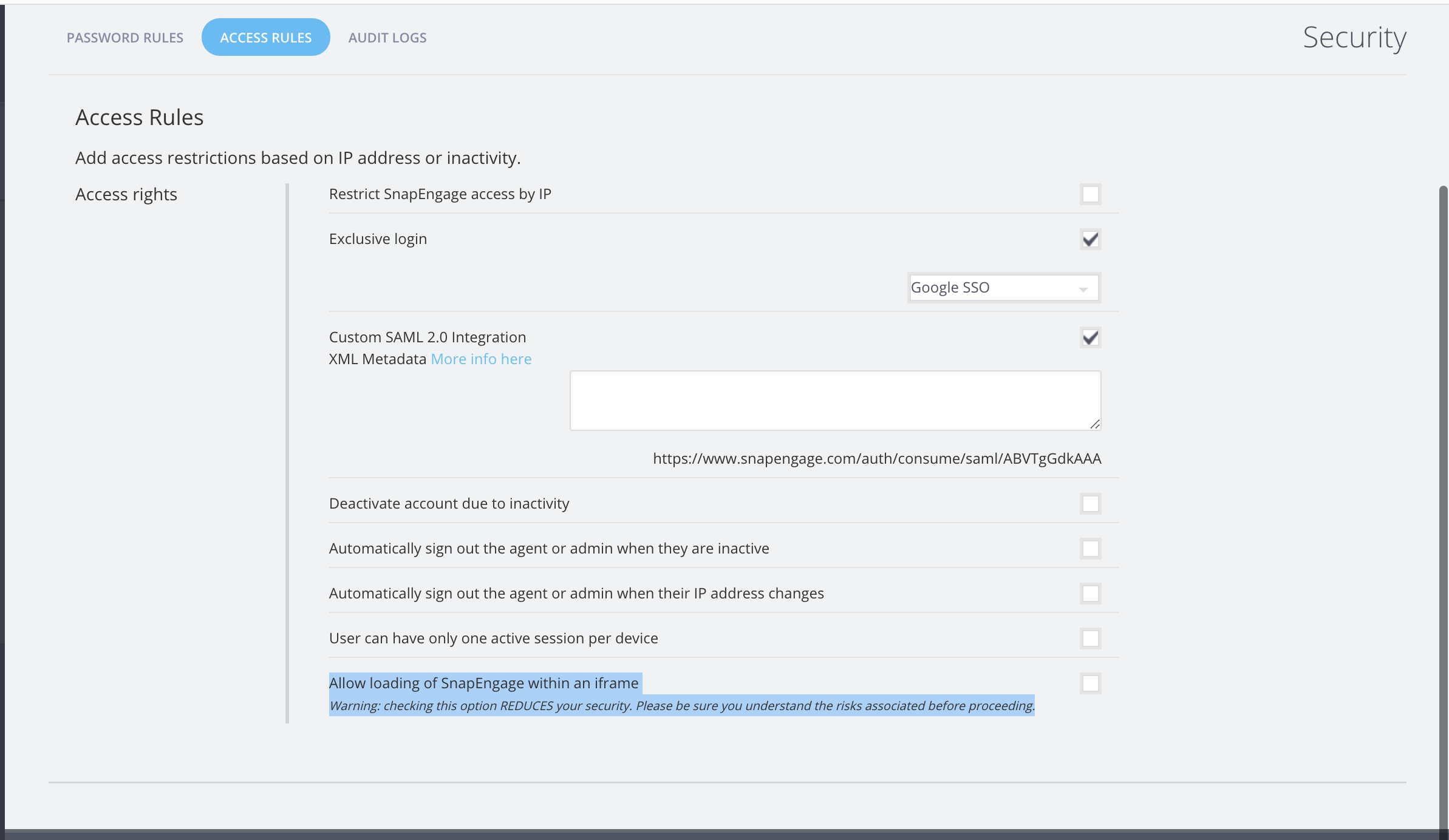
Note: checking this option REDUCES your security. Please be sure you understand the risks associated before proceeding. This option is Enterprise only
Published October 17, 2014