Home > SSO via SAML and Okta with SnapEngage
Categories: Security
(Last Updated On: )
About This Article
The purpose of this article is to provide a comprehensive overview of how to SSO via SAML and Okta with SnapEngage.
With the SingleSignOn (SSO) feature, it is now possible to login to SnapEngage using a SAML (Security Assertion Markup Language) identity provider, rather than logging into SnapEngage with a username/password from our sign-in page. The SAML/SSO feature is available for Enterprise customers.
In a nutshell, SAML is a standard for authentication that allows a user to login one time for separate (all) web sites that require password authentication. Thus, by implementing this protocol, you can have a sign-in process that is easy to hook into from other systems. By providing your team with their SSO accounts, they will be able to login to SnapEngage (and other possible services that you are using) once without having to create and manage different login information and passwords.
By implementing SAML, SnapEngage is not strictly tied to only one SSO provider but can potentially be used with any of them using the SAML protocol. For the time being, Okta is the one provider that we have an established integration with but we would be happy to test any other SAML Single Sign On provider you are using.
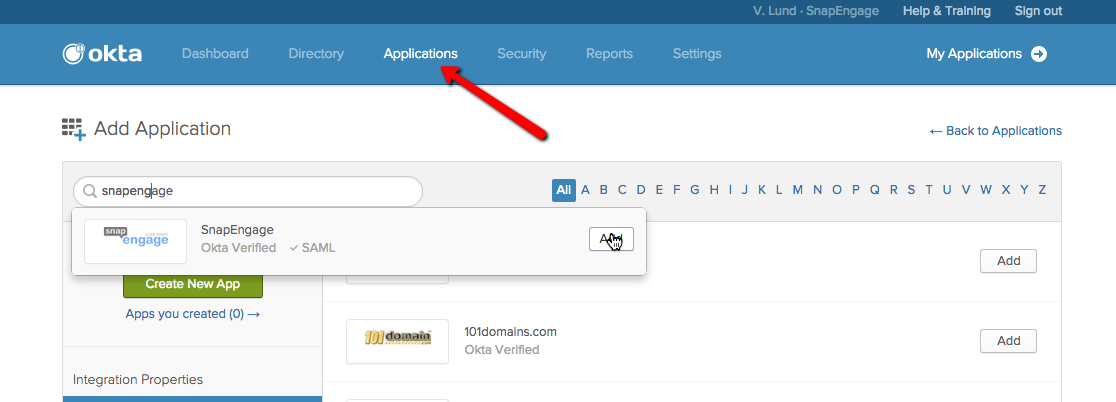
In the Okta dashboard you can add SnapEngage through the administration dashboard; please click on “Admin” and then you will find SnapEngage under “Add Application”.
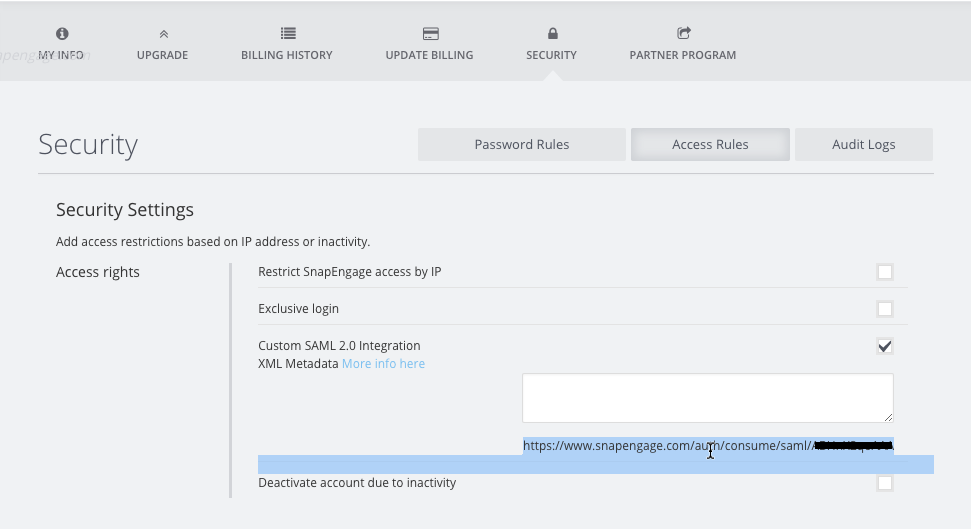
Go back to your SnapEngage account in another browser window and go to: My account > Security > Access Rules. There you will find a url that you need to copy before moving forward.
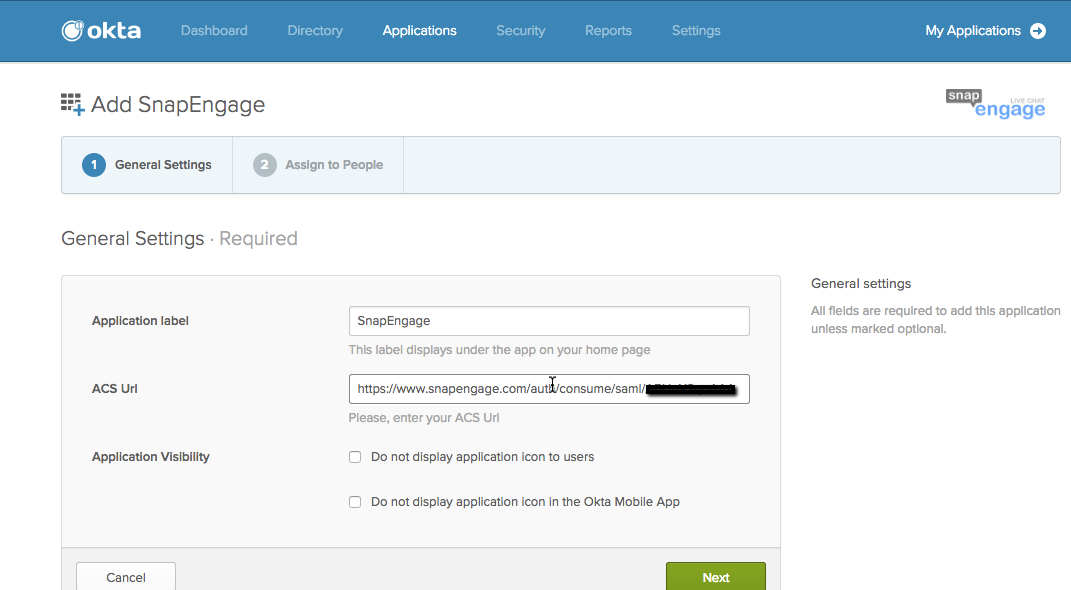
Copy the url from your SnapEngage Account and place it into the ACS Url section of your Okta account.
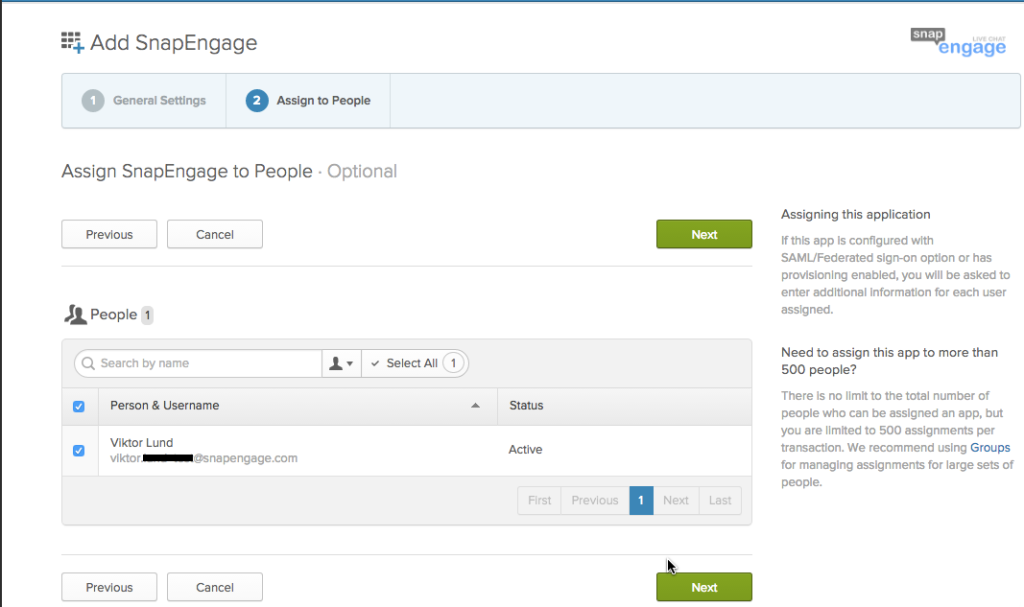
Then click on “Next” so you can assign SnapEngage to your team members. Please be sure to add all team members that use the chat as agents, admins, or other roles.
Please note that you will need to download the “Identity Provider metadata” in the “Sign On” tab on your Okta account and paste the html looking text on the XML Metadata field in the My Account > Security > Access Rules tab
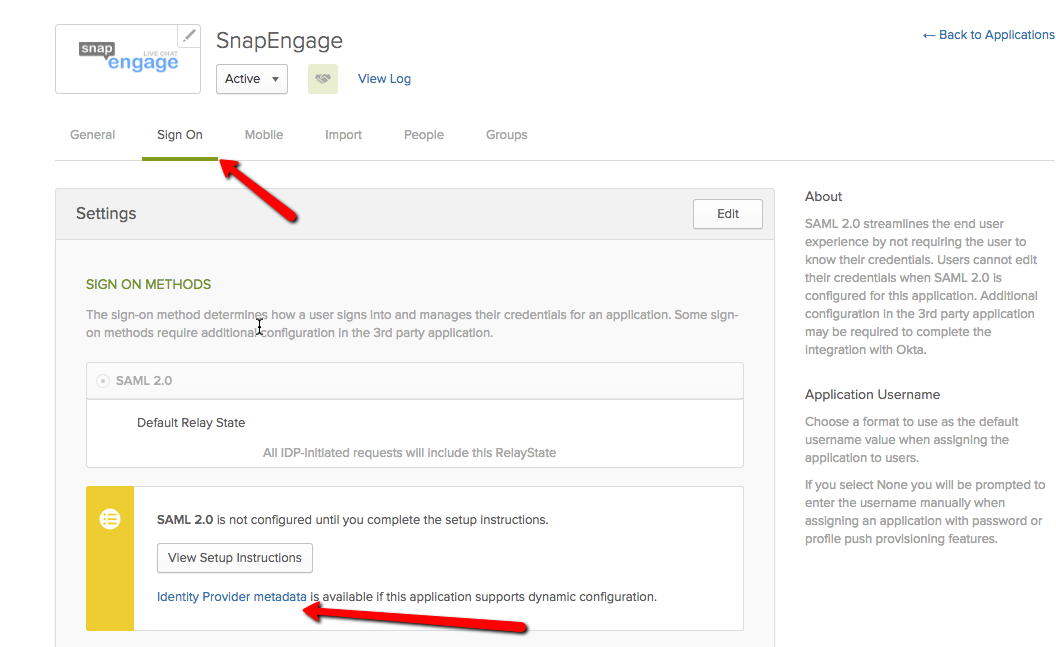
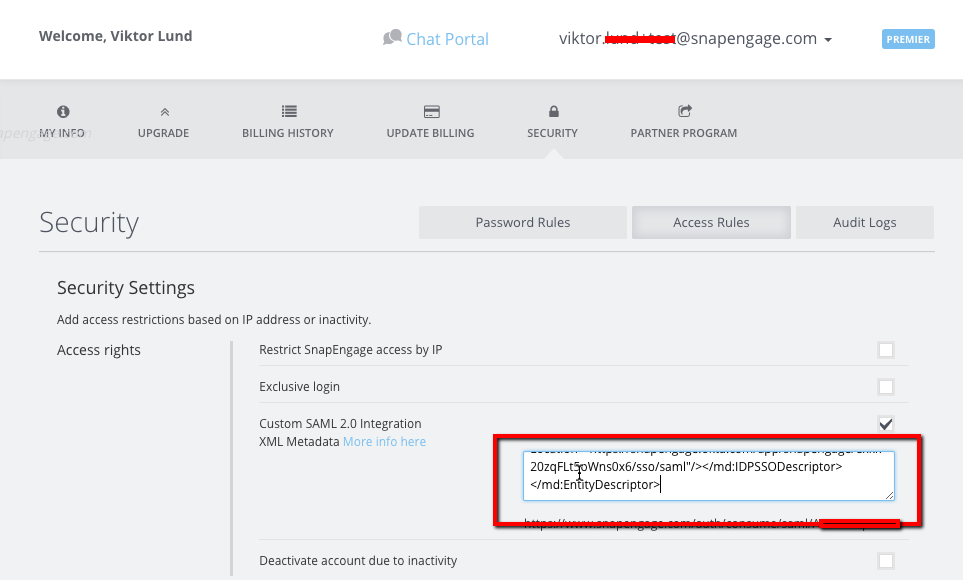
The “metadata” file contains a configuration given by the identity provider that you need to set up in the service provider. That’s why you get all this html looking text that you need to copy and paste in the text input box.
After you save changes you will be able to sign in your SnapEngage account from within Okta…

…and yet another way SnapEngage becomes even easier to use.
Enjoy chatting!!!
Note : Please keep in mind that as soon as the session has the validation, all the security settings (inactivity session, etc…) are still controlled by SnapEngage.
Published October 23, 2015


 (3 votes, average: 3.67 out of 5)
(3 votes, average: 3.67 out of 5)