Home > Visitor Identity verification
Categories: Security | Featured Article
(Last Updated On: )
About This Article
The purpose of this article is to provide a comprehensive overview of Visitor Identity verification.
Visitor Identity Verification is an advanced security and identity protection for businesses that communicate with authenticated users (signed into an application, portal, or other backend system). This feature is available with Enterprise plans. Please come and speak to us if you would like to upgrade.
Clients want to ensure that the person they are chatting with is, in fact, the same person who signed into their systems. Once implemented, this feature will provide a simple indicator to chat agents that the user identity has been verified. This gives agents the confidence to discuss account details, order history, or other information with the visitor.
Our Visitor Identity is stronger and more sophisticated than most other competitors on the market. We use unique, one-time and/or timestamp expiration tokens to ensure that every conversation is verified and not subject to “playback” hack techniques.
Note : Yes, it is the same timestamp that was used in signature creation .
Getting started
In order to do this, your website or app will provide an encrypted HMAC signature for any known user attempting to use chat, along with that user’s identity. On the server-side, SnapEngage will use a secure, secret key to likewise generate an encrypted signature. If the two signatures match, we will display a visual indicator in the Hub to the agent so that they know the identity has been verified. If the signatures do not match, there is some problem or the data has been tampered with, SnapEngage will display a warning to the agent that the user identity has not been verified.
This feature will need to be enabled by a SnapEngage administrator under Settings.
There will be a new setting to turn on Identity Verification, and configure some details that will allow for secure identity verification. The administrator will need to supply the secret token used to encrypt the user identity and compare it to the encrypted HMAC that will be passed to SnapEngage by the client’s website or app.
On the website or app side, identity verification requires our clients to pass an encrypted user hash (HMAC) (that they will need to generate on their server using SHA256) to their widget snippet. This will be passed to SnapEngage as a special Javascript Variable. Additionally, you will need to pass either the user’s email or user_id to perform the lookup, a timeout value, and whether or not the token can be used more than once.
How to enable Visitor Identity Verification
In the Admin Dashboard, under Settings, head over to the Options tab.
Check the box called Visitor Identity Verification.
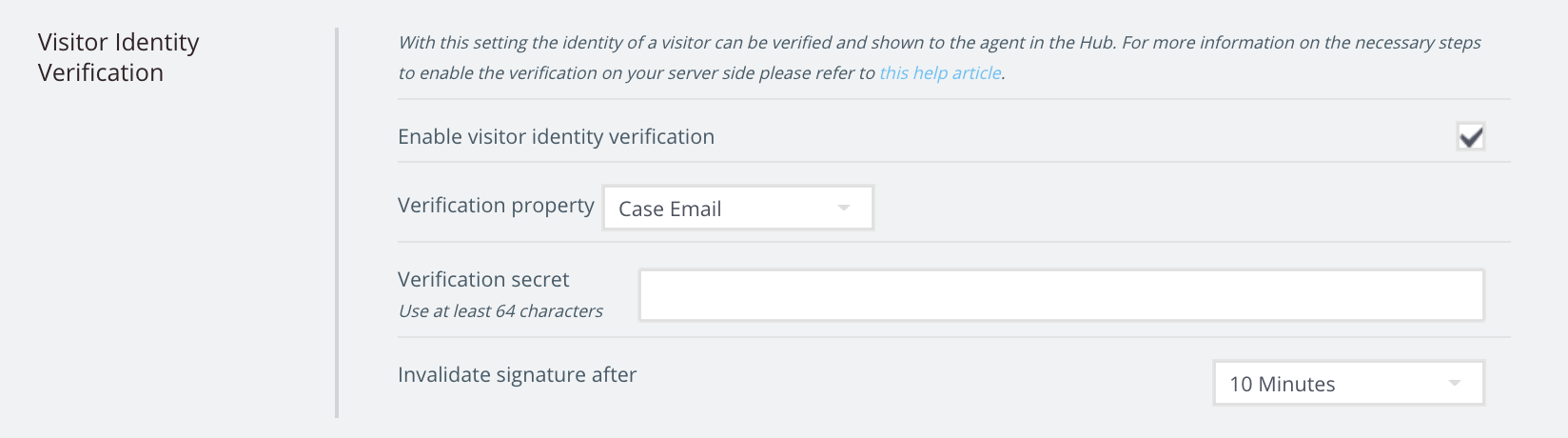
You will need to decide whether you want to use the Case Email as a Verification Property, or a Javascript variable (for example if you use User ID, etc.)
Choose the verification secret, and set a time to invalidate the signature.
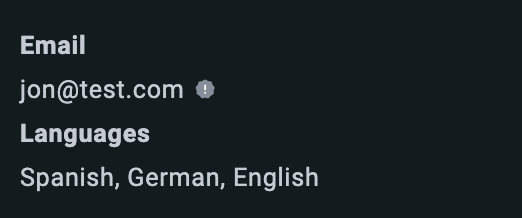
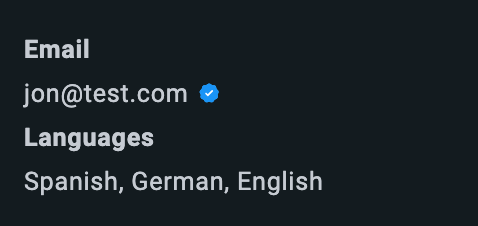
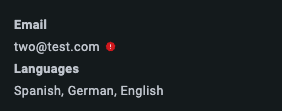
If the visitor’s timestamp has expired, the agent will see a grey tooltip on the Hub (1). If it has been validated correctly, they will see a blue tooltip with a blue tick (2). If it has been tampered with, they will see a red dot with an exclamation mark (3).
The signature is created by concatenating the content that you want to verify + the nonce + the timestamp and then hashing it using the secret that you set up on the admin dashboard.
Note: if you see an expired token for timestamp like image one then try increasing the validation time, it could be the token expired meanwhile they were attempting to validate and increasing the timeframe can help reduce this issue.
You can find the technical documentation here.
var__hmacSignature = signature
var__hmacTimestamp = timestamp
var__hmacNonce = nonce
Published September 16, 2020

 (4 votes, average: 4.75 out of 5)
(4 votes, average: 4.75 out of 5)